Overview:
In today’s fast-paced software development landscape, time is a precious commodity. Every developer strives to streamline their CI/CD pipeline – the automated process that builds, tests, and deploys code. GitHub Actions, a built-in automation champion within your GitHub repository, simplifies building these pipelines with runners. These runners are virtual machines that execute your CI/CD jobs.
While GitHub-hosted runners offer a convenient starting point with a standardized environment, self-hosted runners unlock further control and customization. This blog dives into the world of self-hosted runners.
Empowering Organizations: Deploying self-hosted runners for a robust CI/CD environment
Elevate your CI/CD pipeline with self-hosted runners on GitHub Actions. Organizations can tailor the execution environments within their infrastructure, fostering superior performance and robust security for complex workflows.
Organizations adopting GitHub for their CI/CD pipelines can reap significant benefits by implementing self-hosted runners:
Fine-grained configuration: Provision runners with the specific hardware and software tailored to your project’s requirements. This ensures optimal performance for your unique technology stack. Additionally, organizations can enforce mandatory compliance checks directly on the runners.
Enhanced observability: Deploying self-hosted runners within your infrastructure allows superior monitoring capabilities. Gain deeper insights into the health and performance of your CI/CD pipeline, enabling proactive identification and resolution of potential issues.
Heightened security: Organizations have complete control over the security posture of their runners. Restrict internet access, specific software, and software versions, tailoring the security profile to align with your risk tolerance perfectly.
Cost savings: For large-scale DevOps implementations using GitHub Actions, self-hosted runners can offer significant cost advantages compared to relying solely on GitHub-managed runners. This is especially true for organizations with excess computing resources or predictable workloads.
Key considerations before adopting self-hosted runners:
Self-hosted runners offer significant benefits, but careful planning is essential. Before opting in, consider these key factors:
Maintenance overhead: Setting up, maintaining, and scaling self-hosted runners requires more effort than GitHub-managed runners. This includes infrastructure management, software updates, and security patching.
Infrastructure strategy: Self-hosted runners reside on your infrastructure, granting control but requiring a long-term infrastructure strategy. Excessive reliance on specific cloud service providers might make switching approaches costly or complex later.
Network dependency: Self-hosted runners require a reliable and consistent network connection to communicate with GitHub and other services. Resiliency planning to address potential outages is crucial.
Essential security measures: While self-hosted runners offer greater control, implementing robust security practices and access controls is mandatory to safeguard your infrastructure.
Optimizing your self-hosted runner architecture
Building a robust and scalable self-hosted runner architecture requires careful consideration of several key factors:
Auto-scaling: Dynamically scale your runner fleet up or down based on the number of triggered jobs in GitHub workflows. This ensures optimal resource utilization and avoids unnecessary costs.
Multiple runner labels: Support multiple runner labels as defined by the runs-on field in your action workflow. This allows for granular job execution by matching workloads with specific runner capabilities.
Containerized runners: Consider running your runners in a containerized environment for improved portability, isolation, and security.
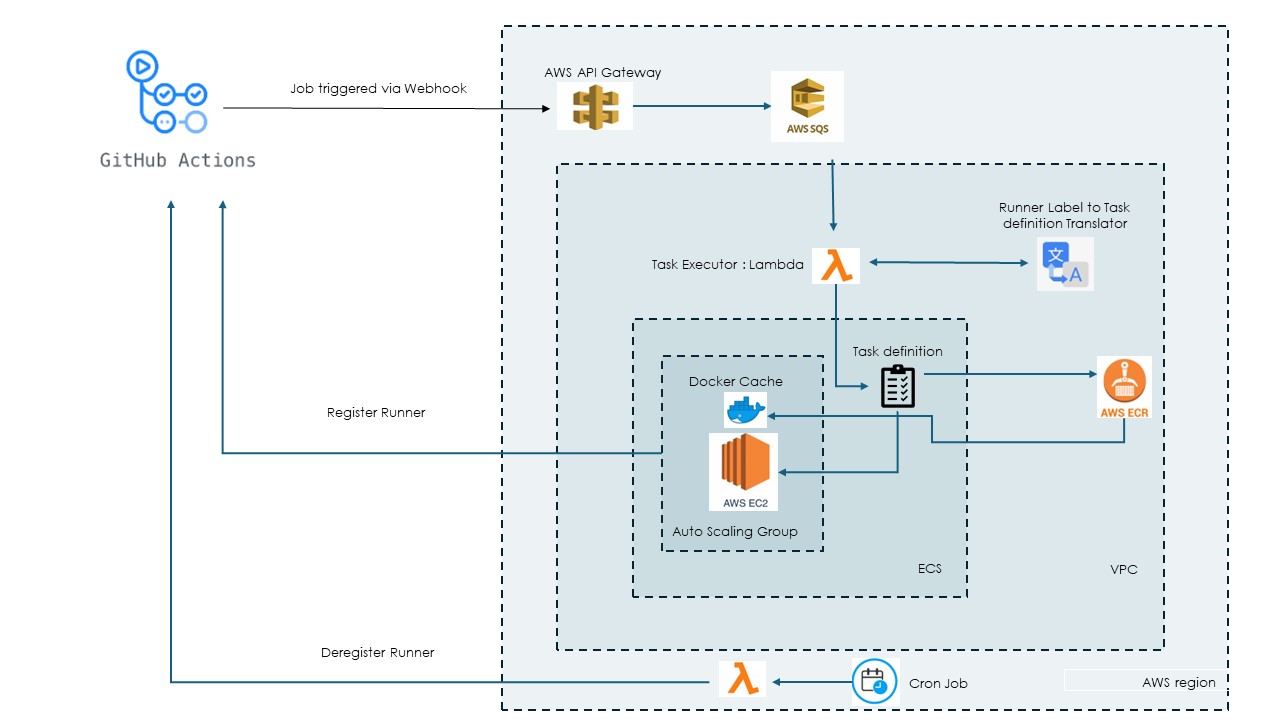
Reference implementation using cloud-based architecture with AWS
Here’s a breakdown of some key components to consider in AWS and their significance in implementing self-hosted runners:
API Gateway: Handles incoming API requests, assists with authentication and authorization, and forwards them to backend services for processing.
Simple queue service (SQS): Acts as a buffer, decoupling service components and ensuring messages aren’t missed, especially during peak loads.
AWS lambda: Serverless functions for tasks like triggering runners based on incoming webhooks.
Elastic container service (ECS): The central component, orchestrating containerized runner deployments. Additional supporting services like Task Definition and ECR (Elastic Container Registry) are often used.:
Flow of execution: Putting It all together
Let’s take a closer look at how your self-hosted runner architecture might work in action. The following diagram showcases an automated workflow triggered by a GitHub webhook.
· When a workflow starts in GitHub, a web request is sent to API Gateway which triggers a Lambda function.
· The Lambda function puts the request in a queue for asynchronous processing.
· Another Lambda function monitors the queue and triggers an ECS task with the appropriate runner image based on the request. The runner then executes the workflow job.
· A separate Lambda function cleans up inactive runners periodically.
Sample architecture diagram
Conclusion:
In conclusion, the choice of using self-hosted runners depends on your specific needs and infrastructure setup. For organizations equipped to manage their infrastructure, self-hosted runners offer a powerful advantage. You can unlock the power of self-hosted runners with GitHub actions to create a CI/CD pipeline that delivers exceptional efficiency and control.