Concept of Metaverse is not well defined and everyone seems to have a different opinion on its possibilities. Metaverse can be considered as an immersive-interactive operating environment distributed on cloud and supported by multiple vendors. Users can access it through various types of connected devices. An interactive layer will be provided on top of internet by using Web 2.0 and Web 3.0 technologies. Metaverse is proposed as an open platform, built on VR/AR/MR/XR environment, in which users can work and play. In Metaverse, the distinguishing factor is that it will allow players to move across virtual spaces with user’s virtual assets seamlessly. Metaverse platform can be used not only by human users but also by smart devices as a layer of communication through which AI and human can share information.
Let us see what type of cyber threats would be of concern in Metaverse.
Metaverse Threats
Predicting cyberthreats for a platform that is still evolving is difficult. By keeping it in mind, what we can do is brainstorming based on current understanding of Metaverse and identify threats inside it and against it. Threats can be classified under categories listed below,
- Non Fungible Tokens (NFTs) : In Metaverse, NFTs are the main candidate for a system to own digital properties. Some of the threat scenarios related to NFTs are
- Integrity Issues could happen. Ownership of assets are regulated by NFTs, but storage for the assets are not provided. This can be exploited for ransomware and other attacks.
- In principle, NFTs are used to verify ownership of digital assets in Metaverse, plenty of things can still go wrong. e.g. Metaverse will use blockchains to verify NFT ownership and blockchains can be hijacked by attackers.
- Malicious actors can trick people who use asset brokers and scammers can defraud people by claiming themselves as legitimate brokers.
- Phishing and spear phishing attacks are possible by using download links for data files.
- Darkverse : Darkverse is similar to dark web and it lives inside the metaverse. Darkverse is more dangerous than dark web as it has pseudo-physical presence of the users. Some of the threat scenarios are,
- Darkverse is created for aiding and planning illegal or criminal activities.
- It can be used as a space for underground marketplaces in metaverse
- Financial Fraud : Large volume of financial transactions will happen in metaverse world and it will draw criminals and criminal groups to metaverse. Possibilities of taking advantage of users, stealing their money and fetching their digital assets are high. Threat scenarios are,
- Metaverse will have a heterogenous digital economy and the exchange rates will be controlled by free market. This free market can be manipulated and exploited by cyber criminals.
- Money laundering could happen in metaverse real estate. Virtual “land” valuation is dependent on perceptions.
- Tax evasion can happen as a company that exists only in Metaverse doesn’t have any jurisdiction.
- Metaverse publishers may create their own in world digital currency, assets and will control the direct supply. This may lead to complicated arbitration process.
- Privacy Issues : Metaverse will be a set of virtual worlds developed and hosted by major players and it will be used by interested persons for free. Even though they claim it as free publishers will manage their meta spaces, gather user’s data and monetize the collected data. Some of the privacy issues in metaverse are,
- User actions will be completely visible to Metaverse operators. To users the service is obviously free but they pay for it with their data.
- Data sovereignty will be an issue as Metaverse is of cloud distributed in nature.
- In an API economy ensuring data sovereignty and maintaining data accuracy is difficult.
- Ample data processing will happen at the user endpoints, such as AR, VR headsets, making them a lucrative hacking target.
- Even though a user can have multiple identities platform can accurately identify the user behind the avatar using parameters such as user behavior and body motion data
- Cyber-Physical Threats : Spatial Web is a computing environment that exist in 3D space and Metaverse will act as an interactive application layer for it. In Spatial Web, coupling of real and virtual realities are enabled through numerous connected devices and they are accessed through VR/AR/MR/XR interfaces. When IoT and cyber worlds are getting integrated that could raise lot of cyber-physical threats.
- Metaverse enables entity-user interactions. It helps smart city infrastructure to communicate with users who wear metaverse-enabled AR glasses. Smart city data can be forged and used to mislead users to make incorrect decisions.
- New classes of IoT and IIoT devices will expose a bigger attack surface.
- Metaverse automations are built on smart contracts and criminals can hack smart contracts or create fraudulent contracts to rob users.
- VR/AR/MR/XR Threats : Metaverse will exist as both VR and MR world. Users will interact inside 3D virtual worlds or with augmented 3D objects in real world. Some threats are,
- Criminals can plan and rehearse real-world crimes by using metaverse virtual world.
- Criminals will copy digital replicas of real-world stores created by businesses to a different metaverse space to deceit shoppers.
- VR/AR/MR/XR applications use location data to connect to localized services. GPS data can be spoofed or a third-party application can send unauthentic location data to users or programs to trick them.
- Social Engineering : Social engineering attacks describe a broad range of malicious activities that are accomplished through human interactions. It requires psychological gimmicks to fiddle users into making security mistakes. Some threat scenarios are,
- Metaverse operators will collect personal data and they can perform precise sentiment analysis on it. e.g. Political parties trying to understand public opinion during elections.
- Criminals can portray service providers like engineers and give false professional advice to people in return for payment.
- Traditional IT Attacks : Metaverse will utilize usual hardware and they are subject to traditional IT attacks such as Distributed Denial of Service (DDoS) attack, ransomware attack, API attack etc.
- Miscellaneous Threats
- Law enforcement agencies will not be able to easily intercept metaverse crimes and criminals
- Environmental impact. e.g. Bitcoin mining consumes lot of electricity
- Network partitioning
- Copyright infringements
- Interaction with bots or AI require ethics, responsibilities, and accountability
- Moderation of speech and activities
Final Thoughts
All these threats highlight the urgency to develop new security models to protect metaverse applications.




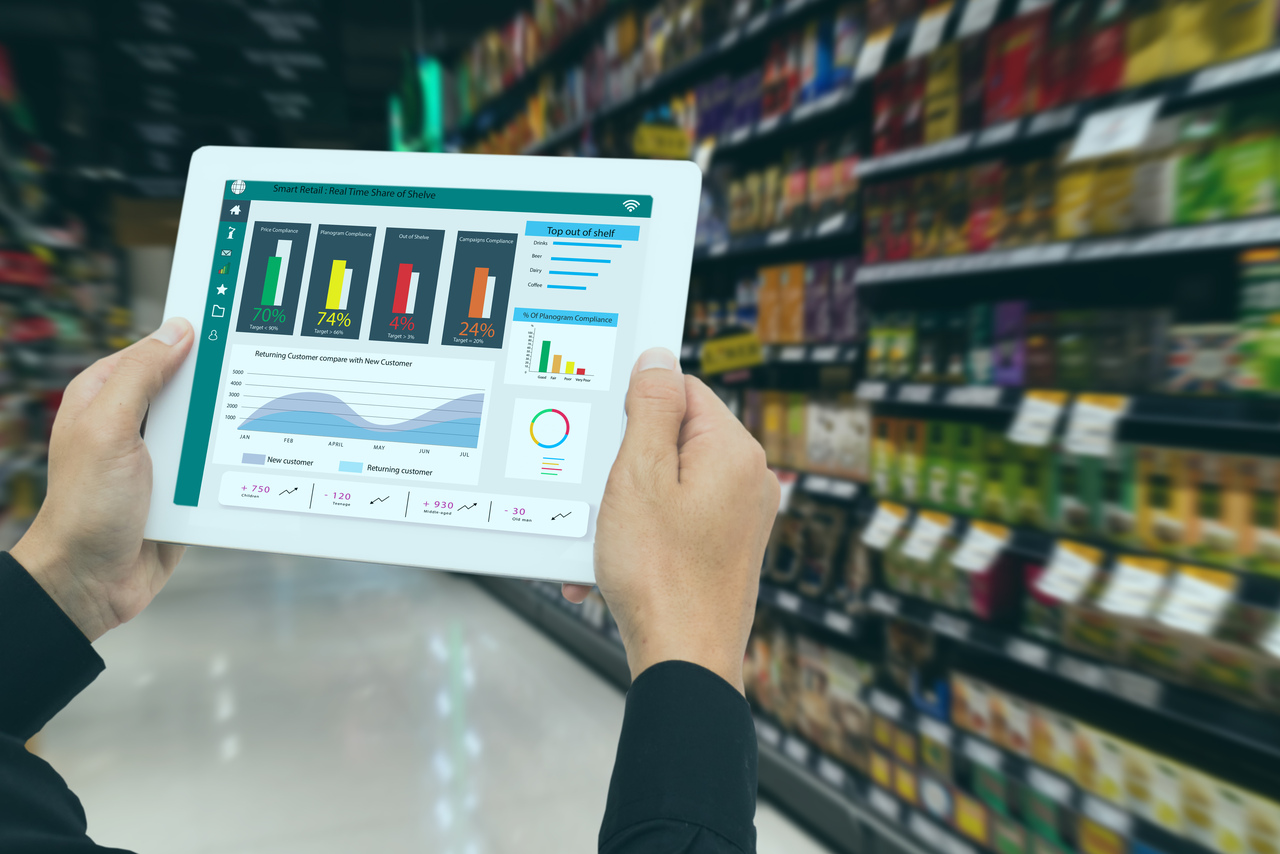





Nice and elaborate coverage of the risks in Metaverse.