Amazon Web Services has offered a new service called Security Lake. This service allows you to store all security-related data from SaaS, on-premise, and cloud sources in a single place, allowing the organization to query and summarize this data to get the complete security posture. Security Lake standardizes data stored from different types of security source providers using the Open Cybersecurity Schema Framework (OCSF).
Handling Logs
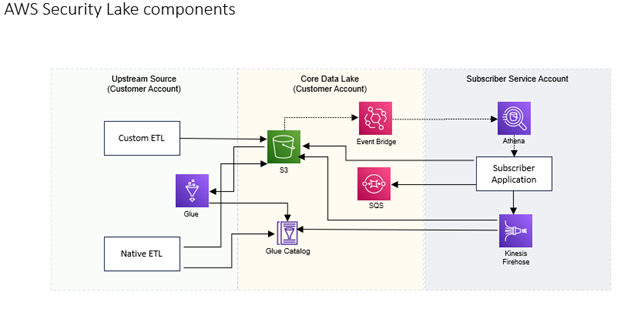
Log Sources (Upstream Sources) can come from Amazon Security components like cloud trails, audit logs, and network logs. These log sources flowing into the system are cataloged and stored in an S3 bucket in OCSF format. AWS Security Lake also allows custom log sources. Any cybersecurity system can also push logs in OCSF format to the Security Lake.
Subscribers are Amazon Security Lake logs consumers who may subscribe to events from Lake from within the customer’s account, or they can subscribe to services within another AWS account. Amazon Security Lake supplies an API (Application Programming Interface) to coordinate access for subscriber services, most of which are third-party partners.
Amazon Security Lake also supports adding custom security sources. Custom sources must meet the core requirements of an AWS Security Lake. AWS Security Lake supplies an API to register a custom source and set up the foundation, and customers and partners coordinate to populate data into custom sources.
Infosys Cyber Next as a Consumer of Security Logs
We wanted to explore the capability of our Infosys Cyber Next platform to tap and understand any security data source. We developed a small proof of concept (POC) to tap into the Security Lake data offered by AWS.
To understand the data coming from AWS Security Lake, we developed an Open Cybersecurity Schema Framework (OCSF) adapter to translate the data from AWS Security Lake to normalized relational data, which can be stored in a simple database table.
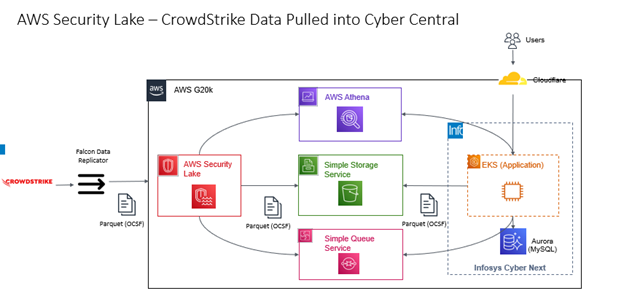
To allow data to be consumed from AWS Security Lake, one must enable the Amazon Security Lake service. Once the Amazon Security Lake Service is enabled, we can subscribe to various security log sources collected by the Amazon Security Lake. In our case, we subscribed to a custom security source from CrowdStrike. Once subscribed to Security Source in Amazon Security Lake, a dedicated queue topic is created in AWS Simple Queue Service (SQS). Once you register, you can listen to the Amazon Simple Queue Service Topic for updates on new events coming from any security source.
Infosys Cyber Next can understand and process data from CrowdStrike events. These events can be further processed into a detection and multiple detections of an incident. This information can be segregated for various organizations and visualized in charts, tabular, and ML-driven predictions.
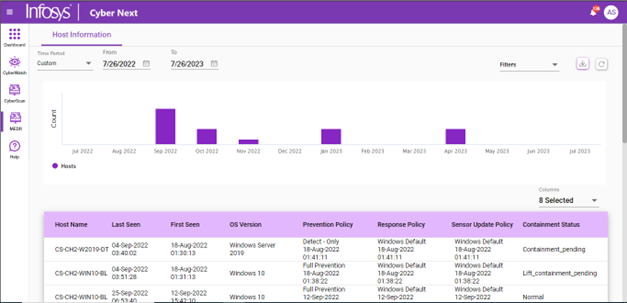
Cyber Next Portal
Infosys Cyber Next has the capability to integrate with Glue API to query the stored data. This allows Cyber Security Analysts to hunt security events and analyze them.
Data Flow
CrowdStrike pushes event data into Amazon Security Lake by registering as a custom security source. The data is pushed into OCSF format. Infosys Cyber Next can then subscribe to AWS Simple Queue Service (SQS) topics. The message received from Amazon Simple Queue Service contains references to files in AWS Simple Storage Service (S3). The files are in parquet format, having OCSF data. Cyber Next reads this event stream data stored in OCSF format in a Parquet file and stores it in its data source. Amazon also supplies its own Amazon Athena that can be used to query security data stored in S3 buckets.
User Access to Data
Infosys Cyber Next allows restricted and secured (via Cloudflare-generated certificate for a machine) access to the data stored in the application. The multitenancy feature of Infosys Cyber Next allows data to be segregated into different schemas per tenant or different databases per tenant. The data stored is encrypted at rest and in transit.
Conclusion
Amazon Security Lake acts as a reservoir to collect various security data for an organization. The capability of Amazon Security Lake to consume data from Amazon Security sources and custom security sources makes it a stop for all security data stored in a common format. The consumer subscription model of Amazon Security Lake makes it easy for any authorized application to access security data from various sources. It is a robust tool to store, access, and query security data.








